Security in AWS is a big deal, and it’s a team effort. Think of it like a potluck dinner—AWS brings the main course (the cloud infrastructure), but customers need to bring their own dish (security measures) to the table too. Now, imagine this potluck is your digital world, with a variety of components like virtual machines, disks, clusters, and crucial data. Keeping all these parts safe and sound is a top priority for any savvy cloud user.
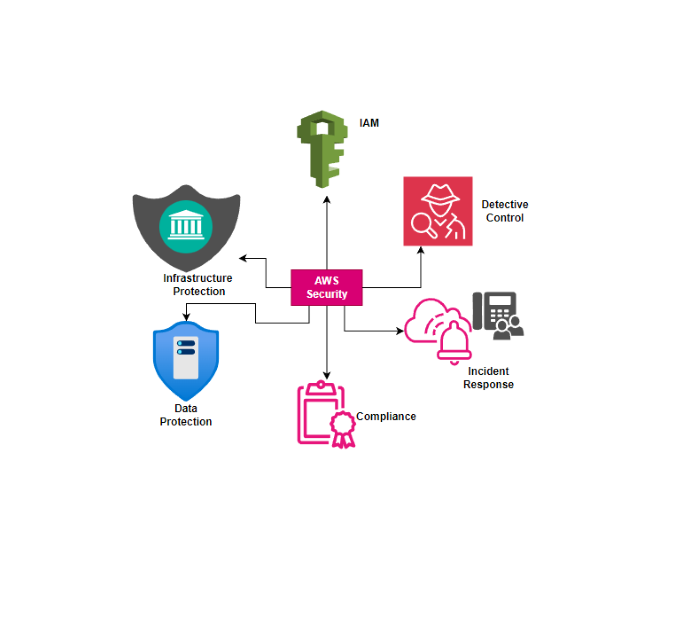
AWS has got your back with a security toolkit divided into six key areas:
- Identity and Access Management: Who gets in and who doesn’t? This domain manages user access and permissions.
- Detective Controls: Like digital detectives, these tools sniff out any suspicious activities or potential threats.
- Infrastructure Protection: Locking down the actual hardware and software that make up your cloud environment.
- Data Protection: Ah, the star of our show! This is all about keeping your precious data safe from prying eyes and sticky fingers.
- Incident Response: When things go south, how do you handle it? This domain focuses on the game plan for when security incidents happen.
- Compliance: Making sure you’re following all the rules and regulations, keeping regulators happy.
Today, we’re diving deep into the world of data protection. What exactly is it? Well, think of it as your data’s personal bodyguard. It shields your important information—like personal data, financial records, and top-secret formulas—from any threats like hackers or accidental leaks.
Why is data protection such a big deal? For starters, it’s the trusty shield that keeps your business reputation intact and prevents those dreaded financial losses from data breaches. Plus, it’s not just about keeping your data safe—it’s the law! You’ve got to comply with all those pesky regulations to stay on the right side of the legal line.
So, let’s talk AWS data protection services—your data’s new best friends in the cloud:
Amazon Macie: Imagine Amazon Macie as your own personal data detective, equipped with the latest in machine learning and pattern matching technology. Its mission? To uncover any hidden treasures (or potential threats) lurking within your Amazon S3 environment.
Picture this: Macie is constantly patrolling your S3 buckets, like a digital security guard, checking for any weak spots or vulnerabilities. If it spots something fishy—like unencrypted buckets or ones that are wide open to the public—it’ll sound the alarm and alert you pronto.
But Macie doesn’t stop there. Oh no, it goes above and beyond. It dives deep into your data, scanning each and every file for sensitive information like your personal identifiable info (PII). And just like a top-notch investigator, it creates a detailed map showing you exactly where your sensitive data is hiding across all your accounts.
But wait, there’s more! Macie even gives each bucket a sensitivity score, so you know which ones need extra protection ASAP. It’s like having your own data security superhero, working tirelessly to keep your digital kingdom safe and sound.

AWS Key Management Service: Imagine AWS Key Management Service (KMS) as the master keyholder to your digital fortress. It’s like having a central command center where you control all the cryptographic keys that keep your data safe from prying eyes.
KMS seamlessly integrates with other AWS services, making it a breeze to encrypt your data and control who gets access to the keys that unlock it. Think of it as the gatekeeper to your most sensitive information.
But KMS doesn’t just stop at handing out keys—it also gives you full control over their lifecycle and who gets to wield them. Need to create a new key? No problem. Want to restrict access to certain keys? Consider it done.
Now, let’s talk about Secrets Manager. Picture it as your personal vault for all those top-secret passwords, API keys, and other sensitive tidbits. With Secrets Manager, you can easily manage, retrieve, and even rotate these credentials throughout their lifecycle.
And here’s the kicker: Secrets Manager doesn’t just store your secrets—it encrypts them too, using those same trusty keys from AWS KMS. So you can rest easy knowing that even if someone were to get their hands on your secrets, they’d be locked up tight in their digital safe.

Secrets Manager: AWS Secrets Manager helps you manage, retrieve, and rotate database credentials, API keys, and other secrets throughout their lifecycles. AWS Secrets Manager encrypts secrets at rest using encryption keys that you own and store in AWS Key Management Service (AWS KMS).

Private CA: AWS Private Certificate Authority (AWS Private CA) is like having your own personal security guard for your digital world. It’s a reliable and flexible tool that helps businesses lock down their apps and devices using private certificates.
Think of AWS Private CA as your go-to for creating top-secret certificates that can identify and safeguard all your digital assets. Whether it’s your servers, apps, users, or even your fancy new smart fridge, AWS Private CA has got you covered.
And the best part? You can tailor-make your certificate and CA setups to fit your specific needs. So whether you’re running a small startup or a massive corporation, AWS Private CA has the tools to keep your digital kingdom safe and sound.

Cloud HSM: Take control of your keys with AWS CloudHSM, where your keys are stored on ultra-secure, FIPS validated hardware. These hardware security modules (HSMs) are like the Fort Knox of the digital world, protected within your very own Virtual Private Cloud (VPC).
But that’s not all—AWS CloudHSM comes with built-in features like separation of duties and role-based access control, ensuring that only the right people have access to your precious encryption keys.
And here’s the kicker: while AWS keeps an eye on the health and availability of your HSMs, you’re the one calling the shots. You have full control over your HSMs, from generating and using encryption keys to managing access and permissions. It’s like having your own personal security team, keeping your digital assets safe and sound around the clock.

AWS Server Side Encryption: It’s like putting your data in a digital safe, keeping it locked up tight.
Certificate Manager: Your one-stop-shop for managing SSL/TLS certificates, keeping your connections secure and trustworthy.

AWS VPN: Your very own private tunnel into the cloud, ensuring your data travels safely and securely.

You can mix and match these services to build the ultimate data protection fortress in the cloud. Whether you’re a small startup or a big corporation, keeping your data safe and sound is non-negotiable. So, until next time, stay tuned as we explore each of these services and how they can keep your data safe in the wild, wild cloud.