Welcome to the digital era – Web 3.0! With the internet reaching every nook and corner of the world, we’re swimming in an ocean of data. Remember the days when gigabytes and terabytes sounded massive? Well, hold on to your hats because now we’re dealing with petabytes and exabytes! That’s a whole lot of zeros and ones.
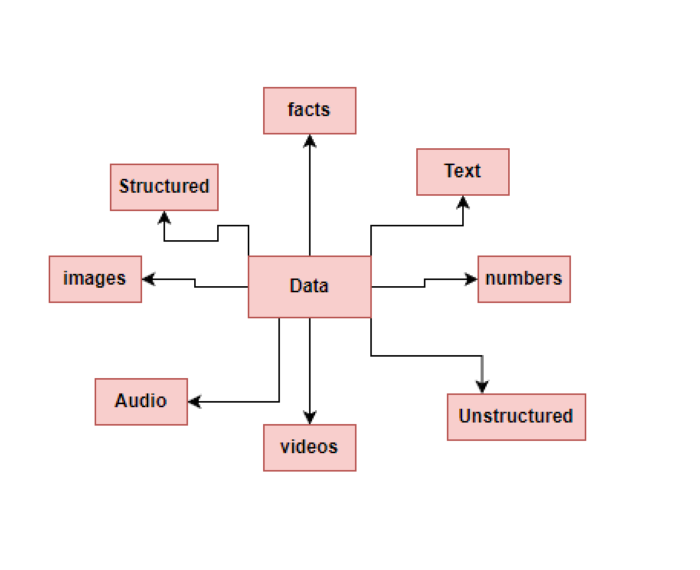
So, let’s talk about this data frenzy. What even is data, you ask? It’s not just boring facts and figures; it’s the whole shebang – text, numbers, images, audio, video – you name it! It can be all structured and orderly in tables or a bit wild and unstructured in natural language or images.
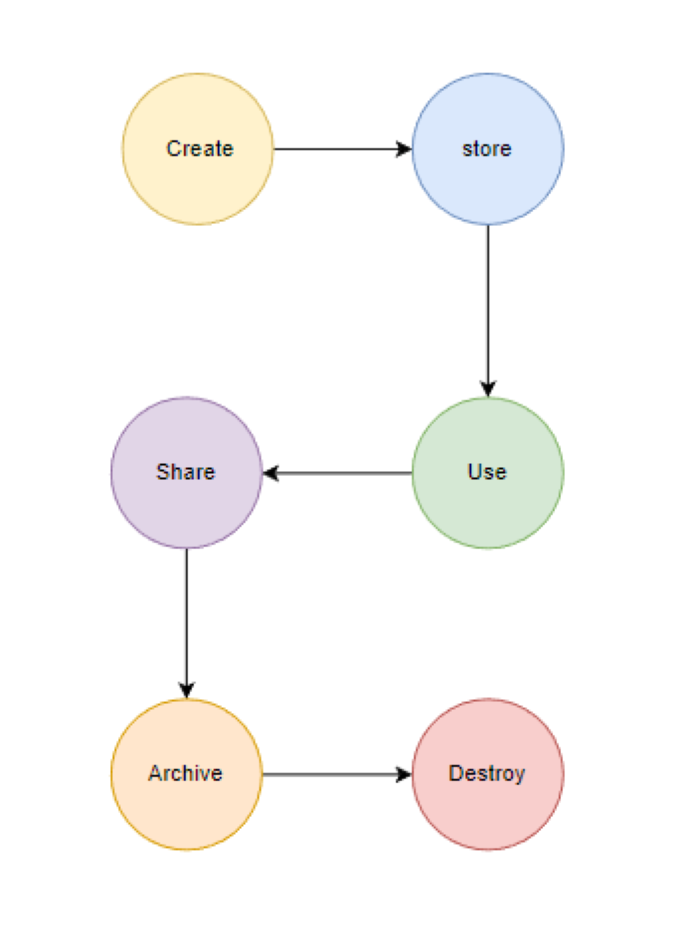
Now, here’s the thing – data has a life of its own. It goes through stages like:
- Create: Someone’s out there generating or tweaking data.
- Store: Boom! It’s committed to a storage repository almost as soon as it’s created.
- Use: Time to shine! The data gets viewed, processed, or used without any fancy modifications.
- Sharing: Sharing is caring, right? The data becomes accessible to others.
- Archive: It takes a bow, leaves the active scene, and settles into long-term storage.
- Destroy: The grand finale – data is permanently obliterated using physical or digital means.
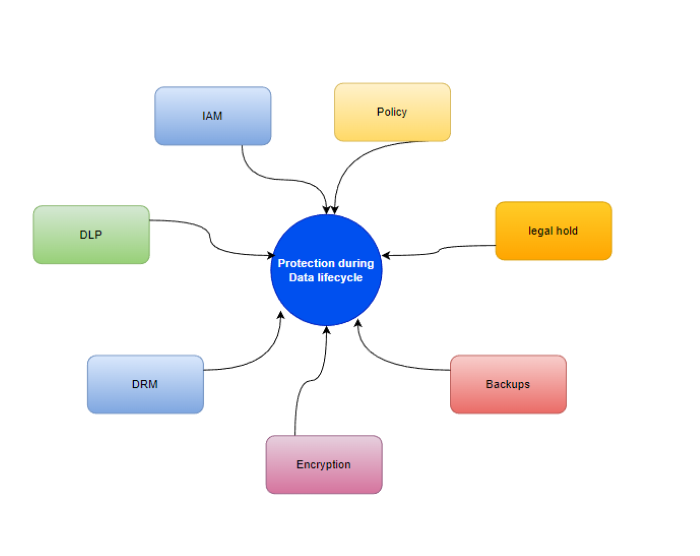
Now, why should we care about this data lifecycle? Because leaks can hit a company like a ton of bricks, bringing financial doom. Protecting data is not just a suggestion; it’s a necessity.
So, how do we shield our precious data throughout its journey? Policies and IAM (Identity and Access Management) are like the bodyguards. They decide who gets access to what data and what they can do with it – create, modify, or just admire from a distance.
Once data hits the stage, it’s stored and protected in two ways – backups and encryption. Backups are like a safety net, saving the day if someone accidentally hits the delete button. Encryption, on the other hand, is the secret agent, guarding the data at rest and in transit.
Enter DLP – the superhero of the digital world! It’s like the bouncer at the club, ensuring that sensitive or confidential info doesn’t sneak out to unauthorized parties. It’s all about preventing unauthorized access, sharing, or spillage of the good stuff.
Then comes DRM, another knight in shining armor. It uses encryption, access controls, and more to keep digital content on a tight leash, making sure only the chosen ones get to enjoy it.
But our data story doesn’t end there. We need policies, archiving procedures, legal holds – the works! These help keep data archived appropriately, complying with the rules of the land and maintaining the good ol’ compliance.
Finally, it’s time for the grand exit – data deletion procedures. Whether it’s a digital vanishing act or a physical shredding session, we’ve got to bid farewell properly.
And there you have it – a whirlwind tour of the data lifecycle and how to protect it using the best practices. Keep your data safe, folks!