Let’s talk about something that might not sound super thrilling, but trust me, it’s the unsung hero of our digital world – Encryption!
In this age of constant digital chatter, where your information is like gold and communication is the name of the game, keeping our data safe from nosy intruders is more important than ever. That’s where encryption comes in – the superhero of the digital realm.
Picture this: Encryption takes your everyday readable data and turns it into an unreadable secret code. It’s like having your secret diary written in a language only you and your best friend understand. How? Mathematical magic with algorithms and keys!
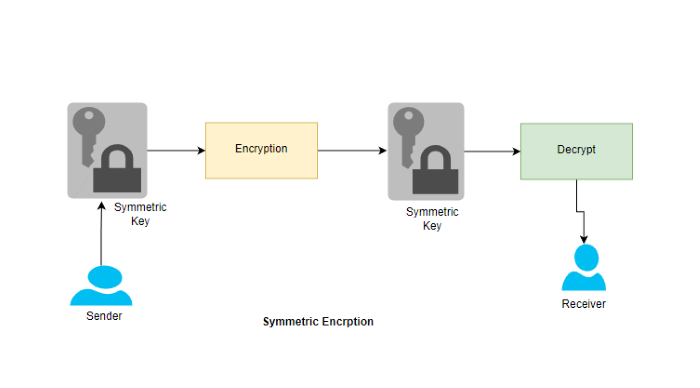
Now, let’s get down to the nitty-gritty and explore the superhero trio – Symmetric Encryption, Asymmetric Encryption, and the mighty Message Integrity Control (MIC).
- Symmetric Encryption – Sharing is Caring (But Also a Bit Tricky): Symmetric encryption is like having a shared secret key for both locking and unlocking your secrets. It’s quick and great for keeping things hush-hush. But, and there’s always a but, managing and securely distributing that secret key is like trying to juggle water balloons – challenging. Enter the Advanced Encryption Standard (AES), the cool kid on the symmetric block.
Asymmetric Encryption – Double Trouble (In a Good Way!): Now, asymmetric encryption spices things up with a pair of keys – public and private. The public key locks up your data, and only the private key can open the lock. It’s like having a secret handshake that only you and your BFF know. RSA and SHA are the rockstars in this asymmetric encryption gig, making sure your data stays VIP-access-only.
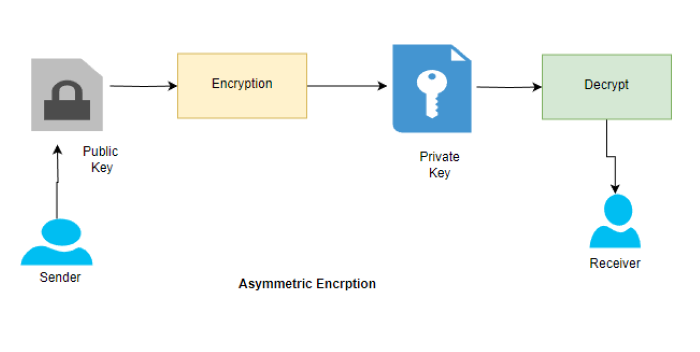
And just think of “Asymmetric” as a fancy way of saying “authentication.” Your private key is like your VIP pass – no pass, no access.
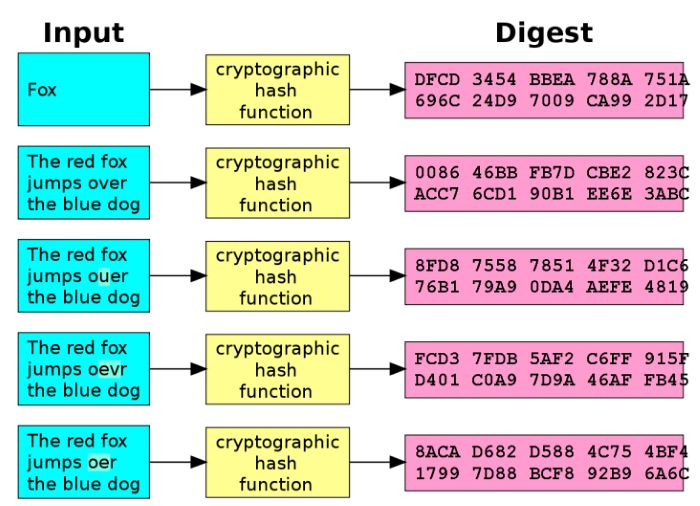
- Message Integrity Control (MIC) – The Data Bodyguard: Imagine MIC as your data’s bodyguard in this wild, wild west of digitalization. It ensures that your messages don’t get a makeover during their journey. How? With hash functions!
• Hash Functions: These geniuses generate unique codes based on your message content. Change a word, and boom, a completely different hash.
• Incorporating Hash Value: The sender computes the hash, slaps it on the message, and sends it over.
• Verification at the Receiver’s End: The receiver double-checks the hash value. Match? All good. Mismatch? Someone’s been tampering.
Encryption: Your Digital Shield and Sword: In our ever-evolving digital landscape, encryption is the shield that keeps our data safe and the sword that slays unauthorized access. Whether you’re into symmetric secrecy, asymmetric handshakes, or MIC bodyguards, encryption is the unsung hero that lets us enjoy the perks of digitalization without compromising our privacy. So, let’s give a digital salute to encryption – our guardian in the pixelated wilderness!